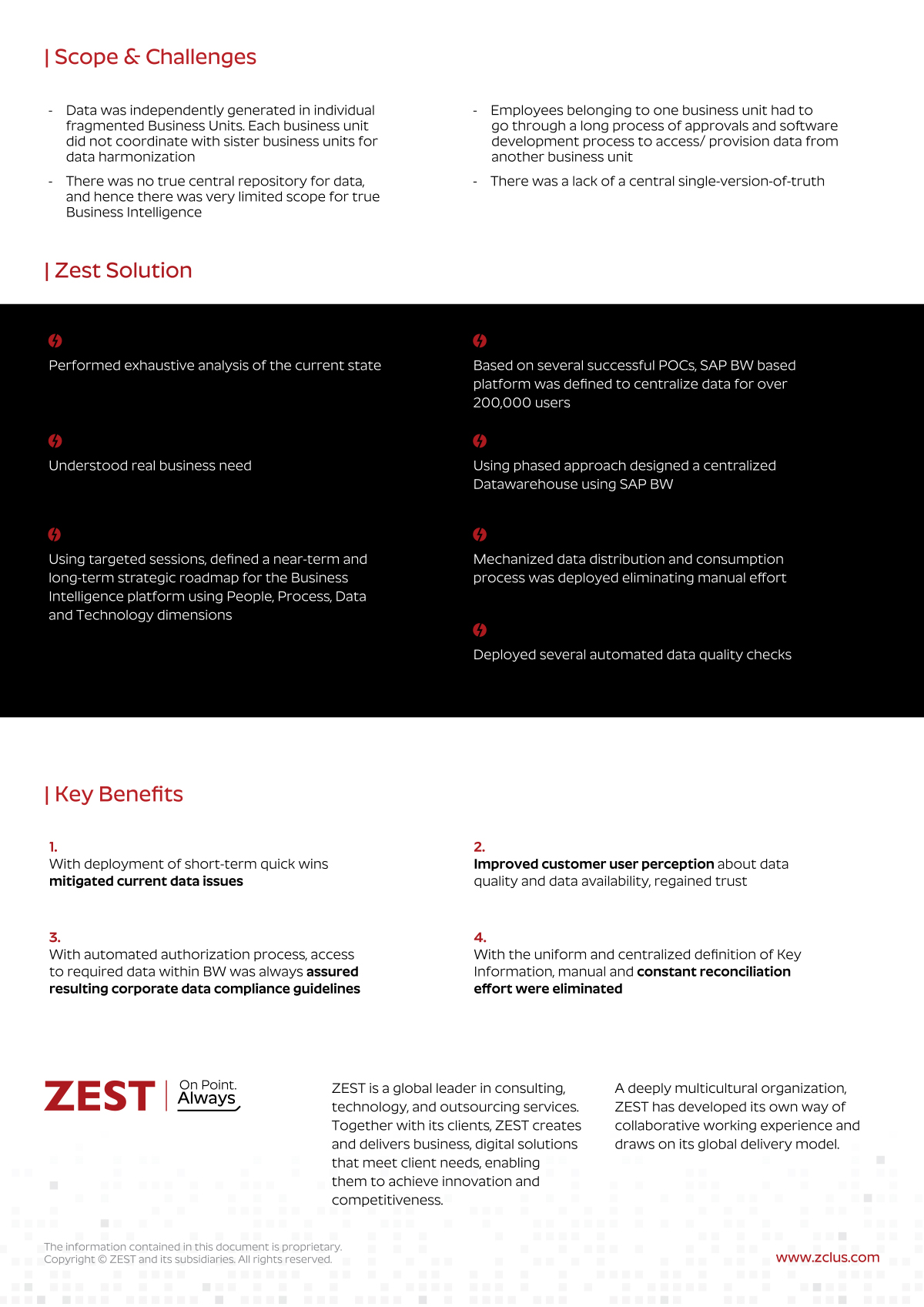
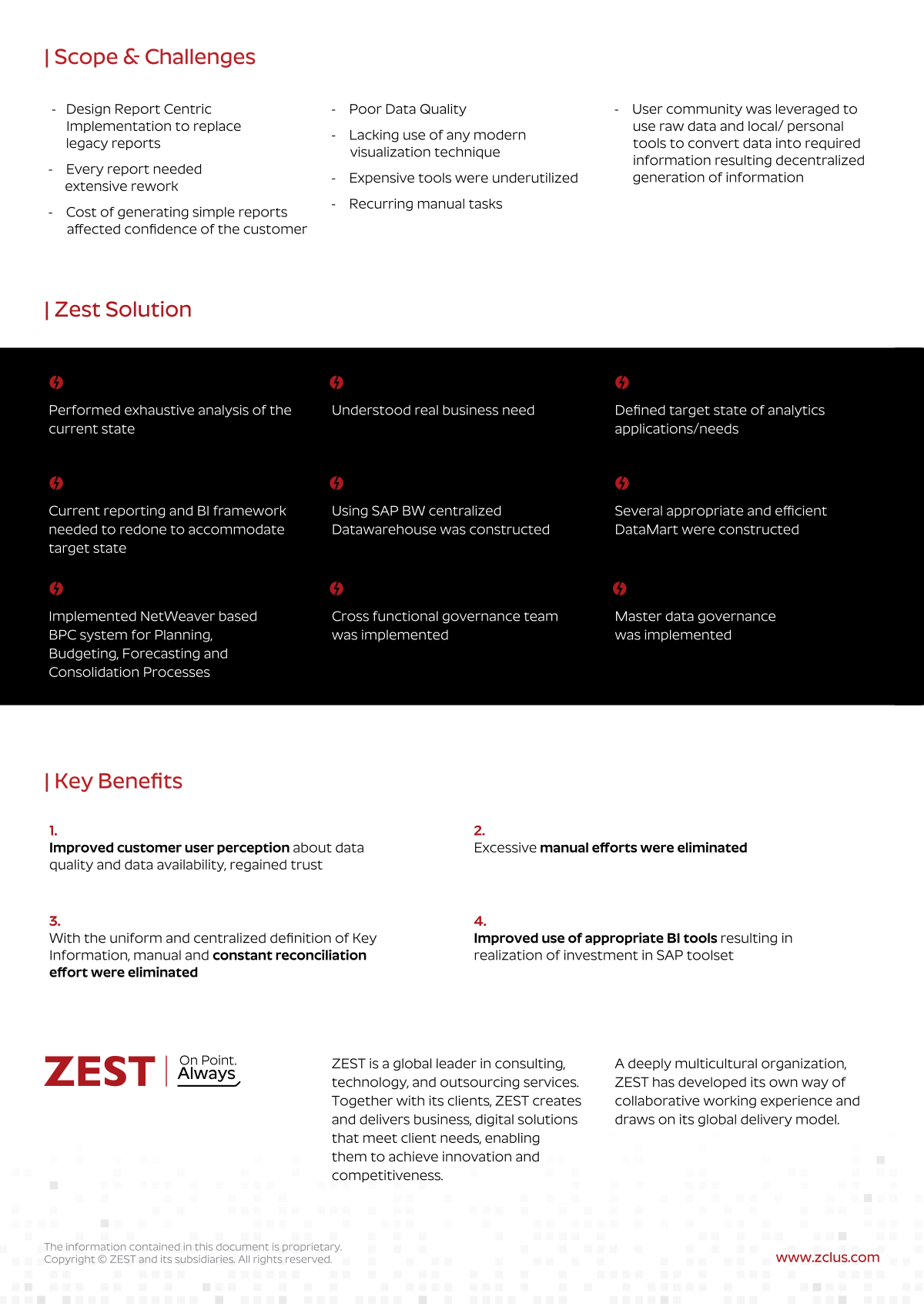
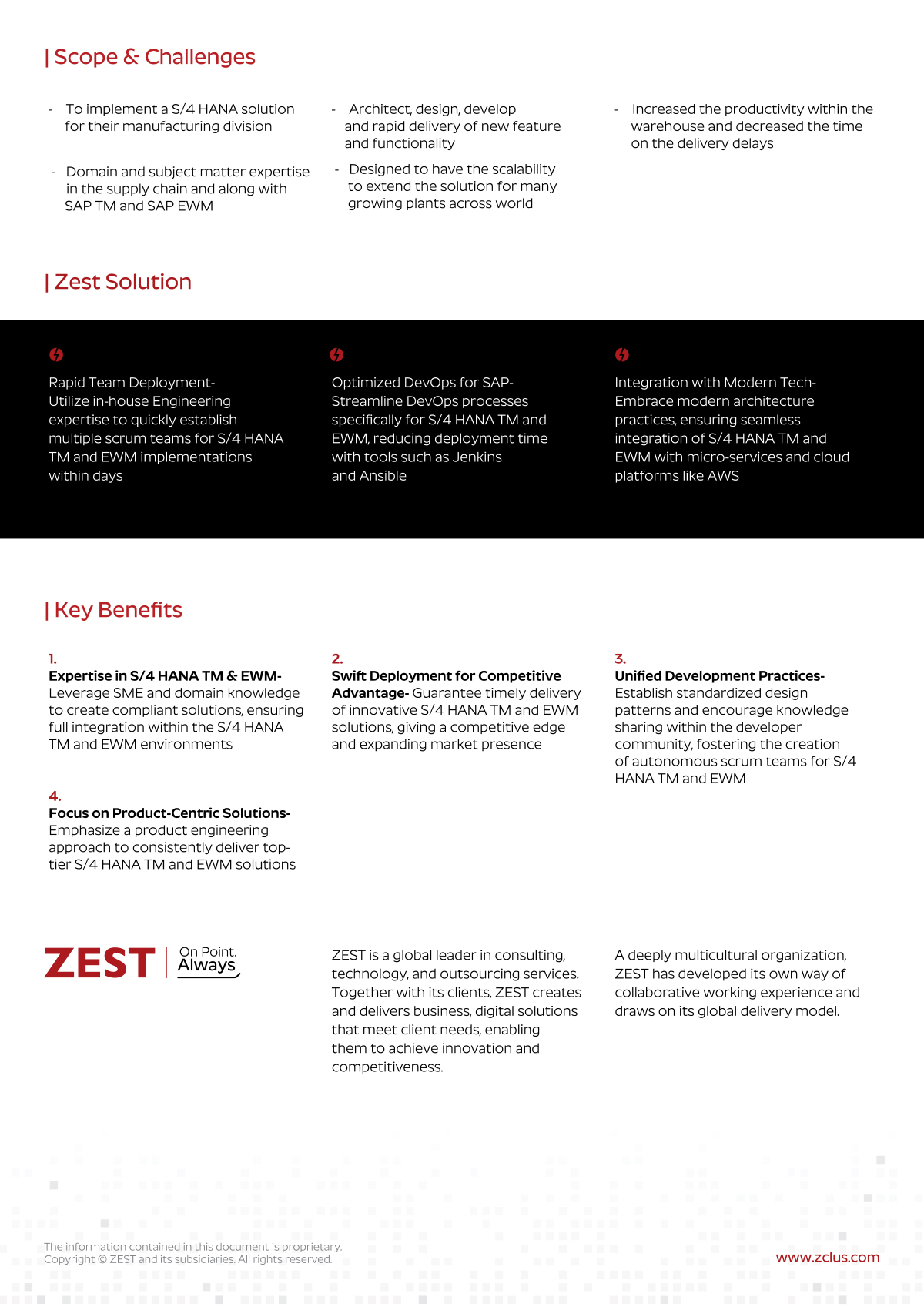
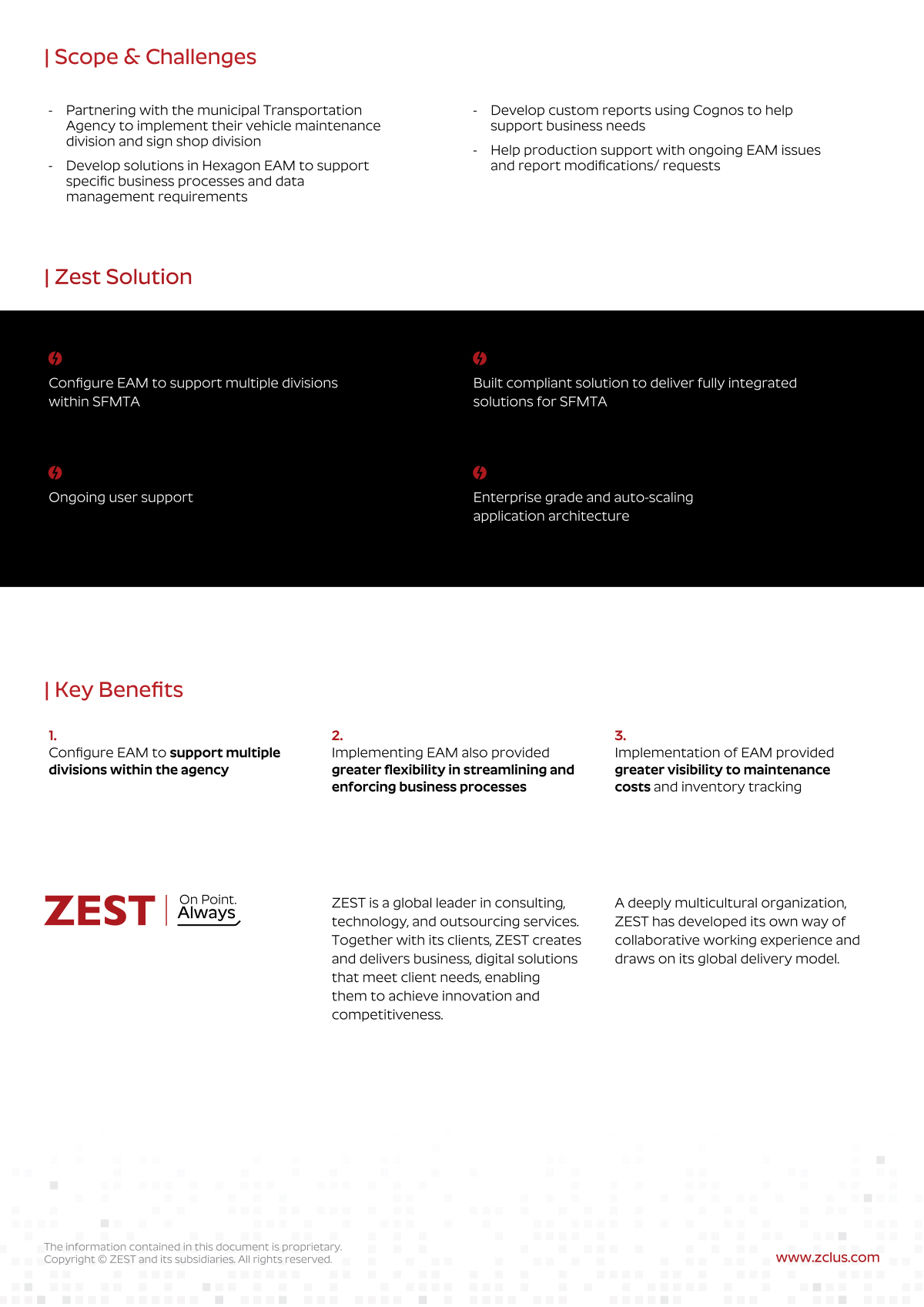
Our approach to technology enables your organization to AIM Higher. Lots of companies can set up your laptops or manage your infrastructure.
In order to contend with today’s challenges, you need more than a break-fix vendor with a “24/7” help desk ticket to nowhere. You need a proactive partner that stops the issues before they start. That’s where ZEST comes in.
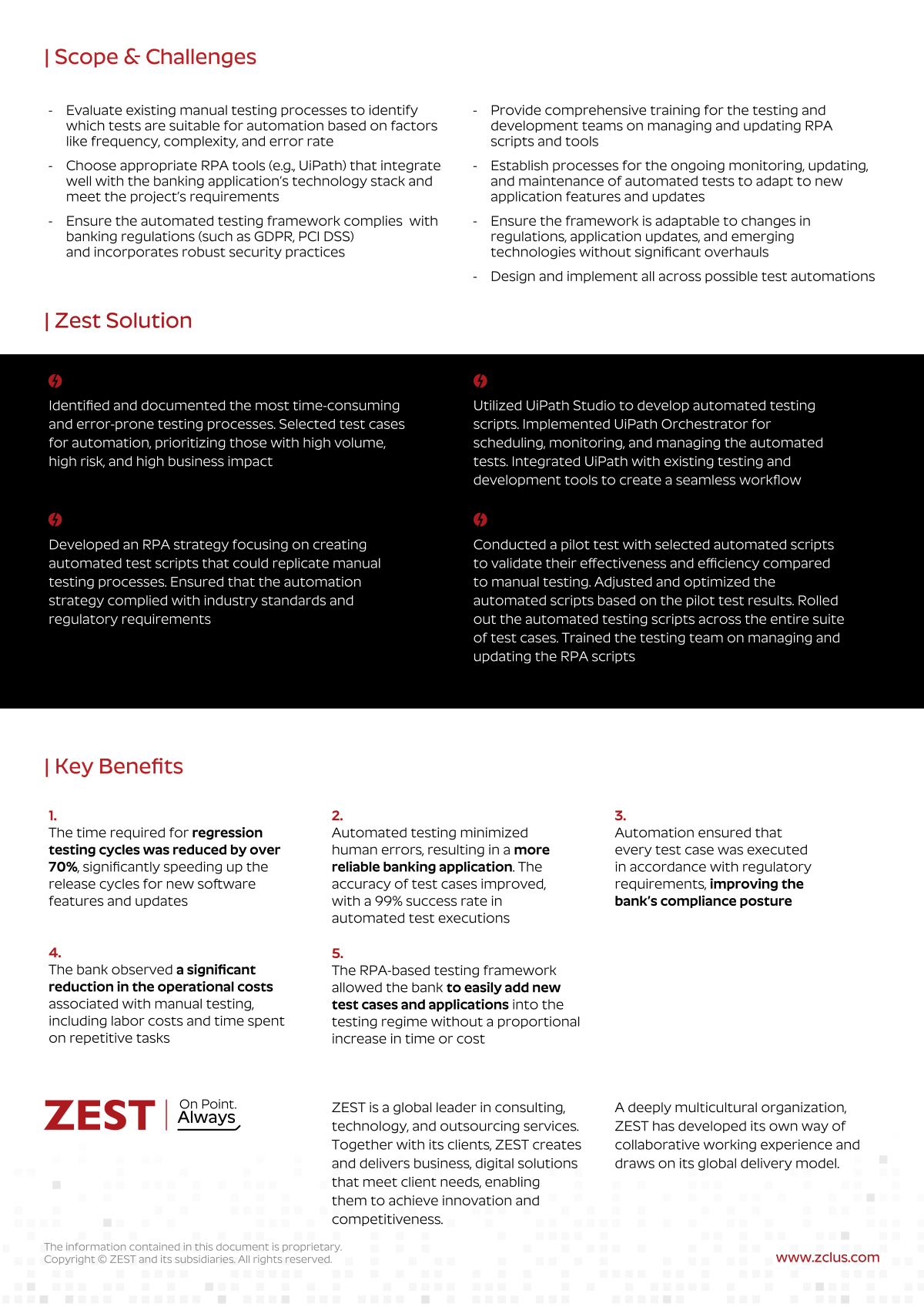
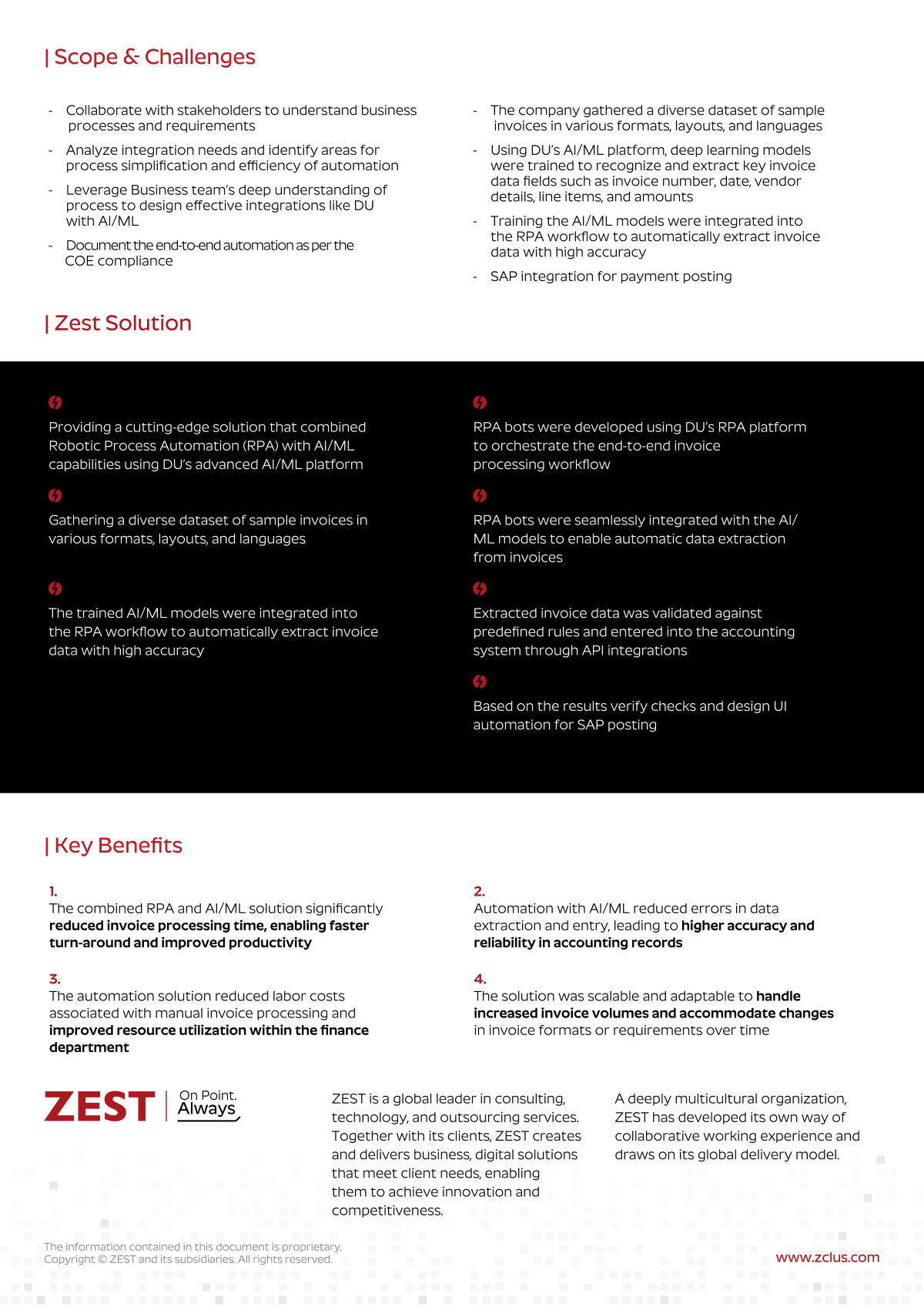
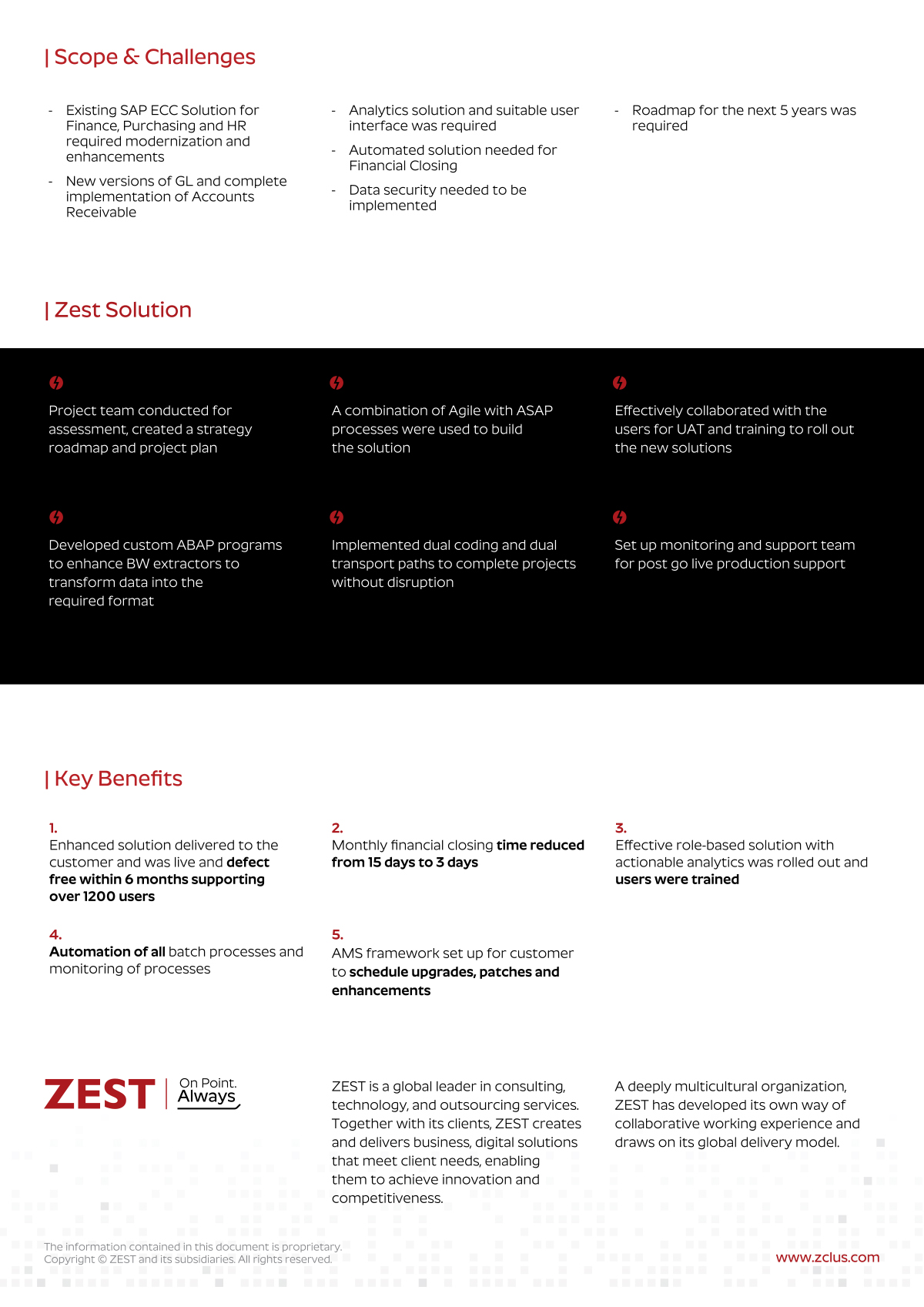
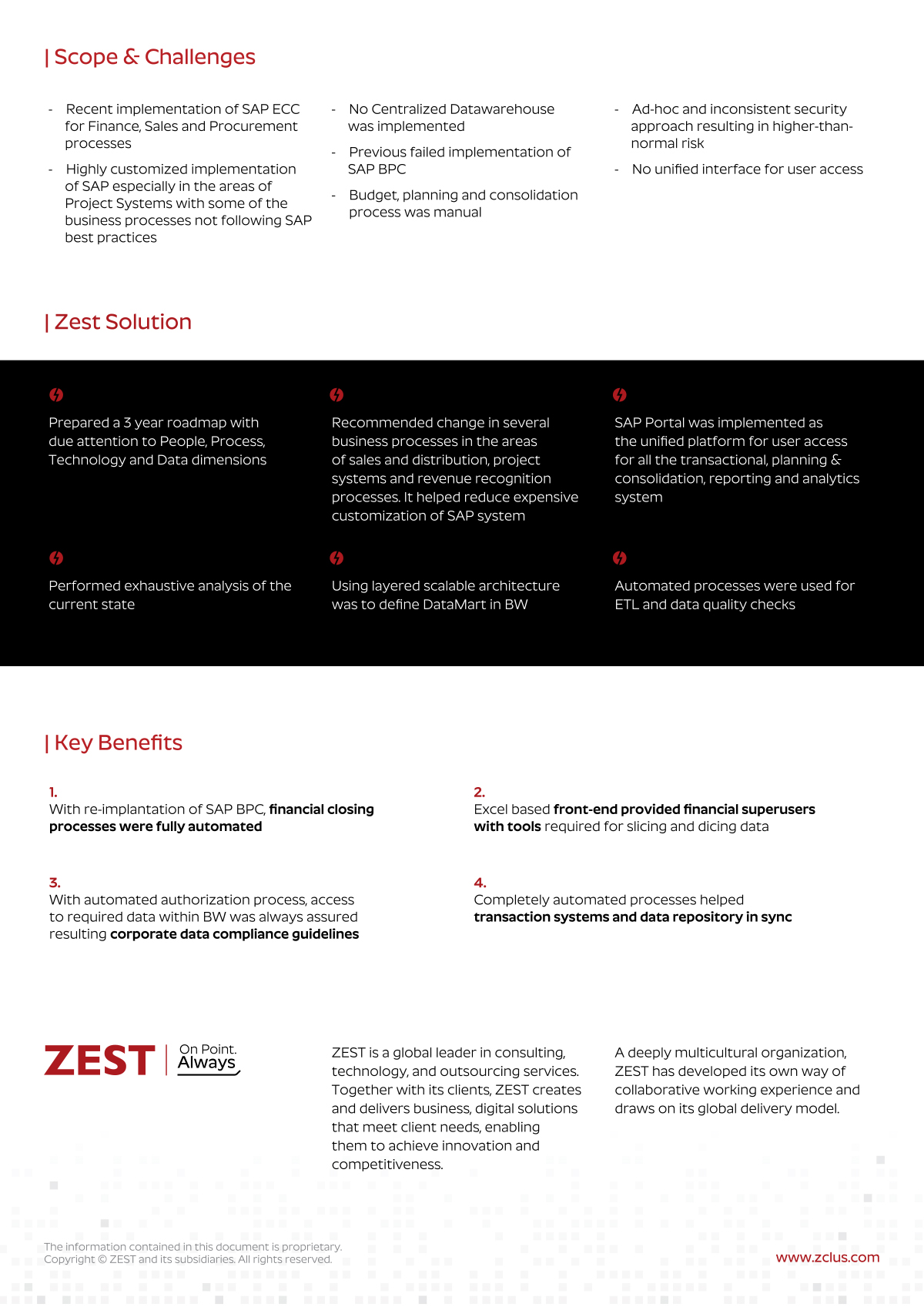
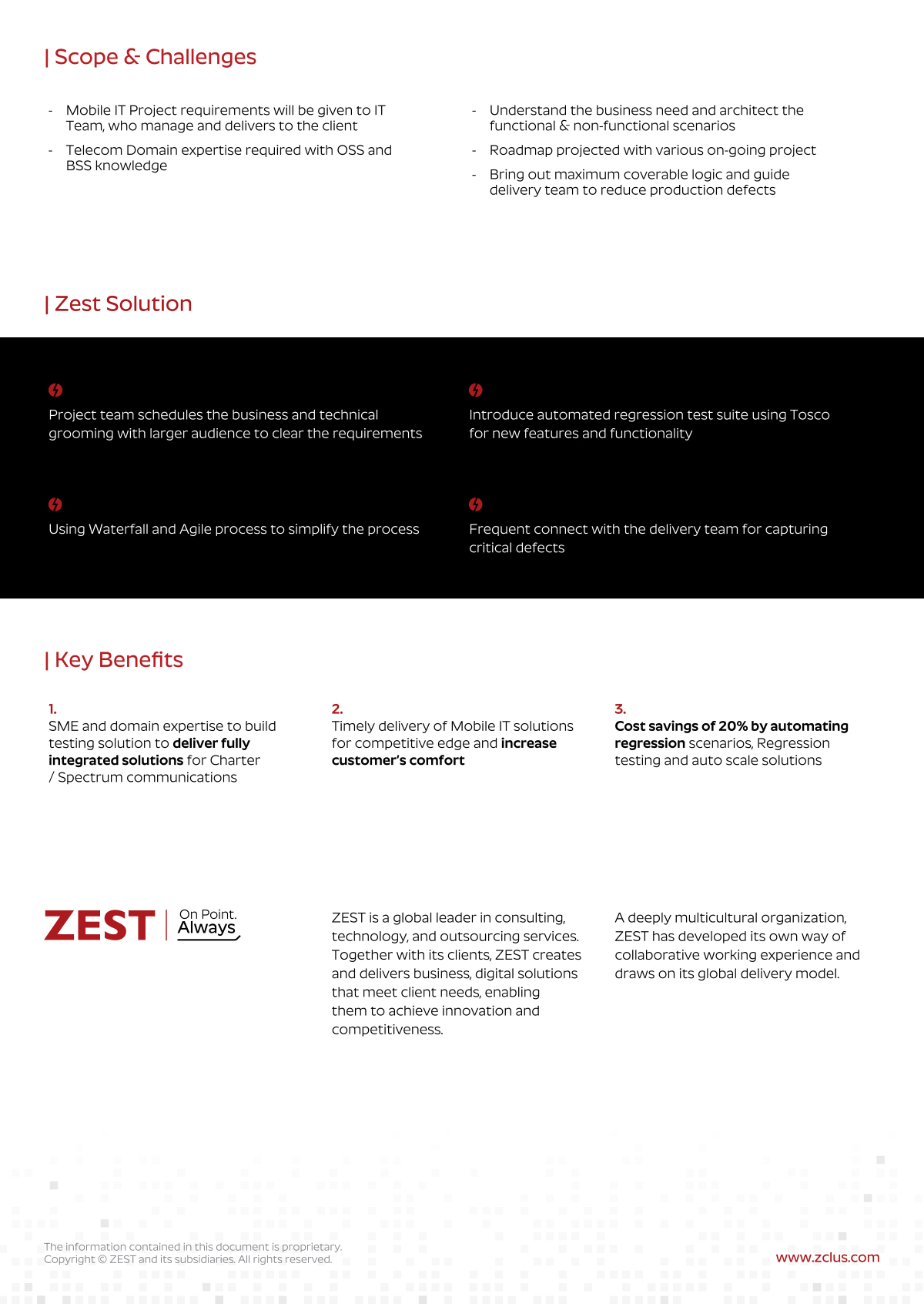
ASSESS
We analyze understanding your current state and then work with you to identify gaps and possible solution paths.
IMPROVE
We replace each business challenge with a solution, filling those gaps and stabilizing your technology infrastructure.
MANAGE
We strive to make IT an invisible enabler for your organization. Our expert team take’s care of everything from updates and patches to end user support, cybersecurity, and data backups.
HIGHER
From strategic guidance on bigger picture digital transformation initiatives to managed security, a modern website, insightful reporting, and dashboards for your teams.
Cybersecurity
Use technology to overcome challenges and threats. When needs and budgets clash, it's time to look for a better way to use technology to empower your staff, stay safe in a volatile cyber world, and become more people-focused.
ZEST Cybersecurity practice drives business performance, confidence and trust through the delivery of Cybersecurity services. We enable trust in systems, design and data, so organizations can take more risk, make transformational change and enable innovation with confidence. We achieve this goal through the cybersecurity community which houses strategy, architecture and operating model skills within 5 core cybersecurity competencies that can credibly serve a range of c-level cybersecurity stakeholders.
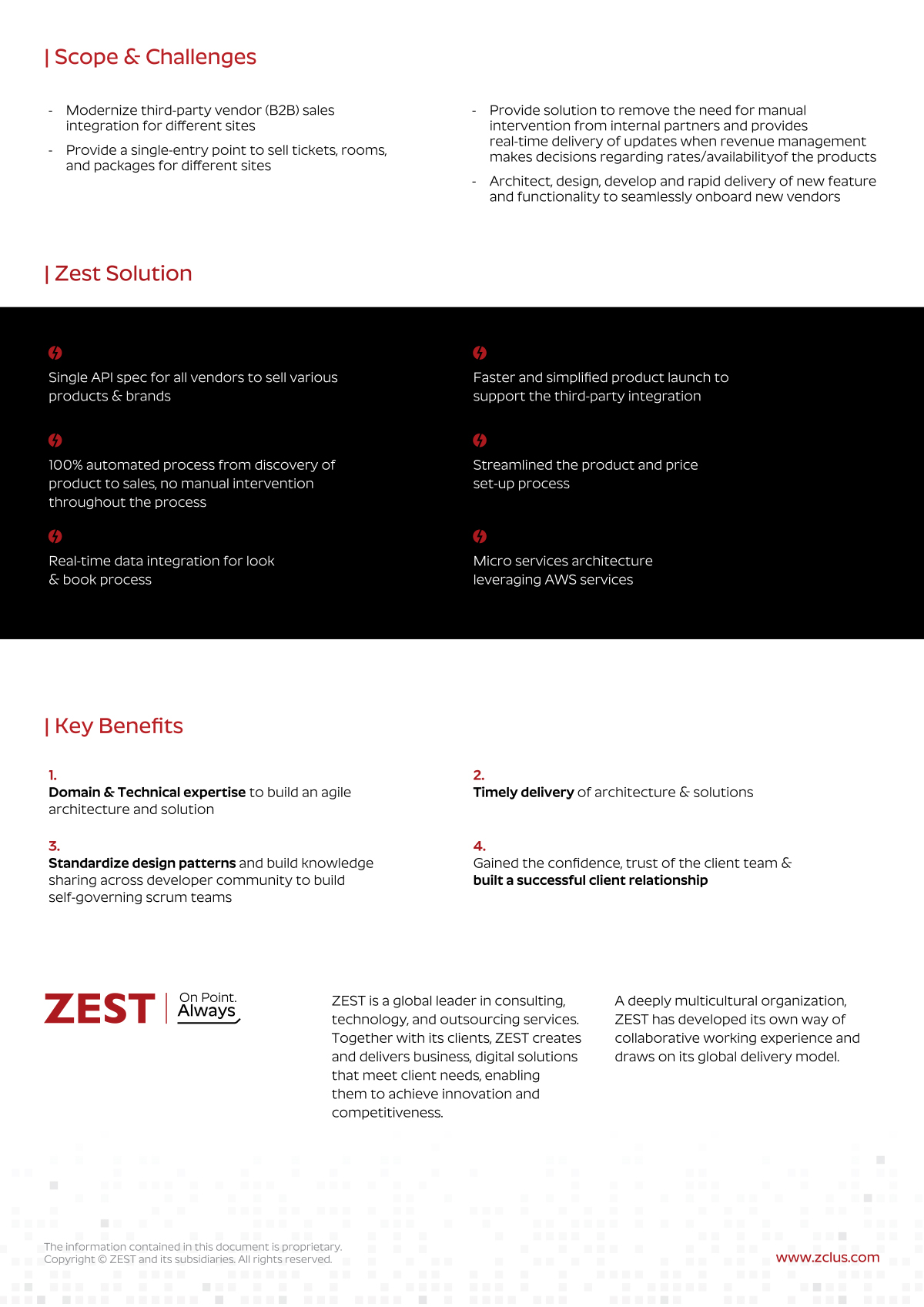
Our Service
Offerings
You need a forward-thinking, practical, and proactive partner. One who can guide you to right-sized solutions that empower you to use technology to drive efficiency and mitigate risk… and one who can help you avoid bloated solutions that drive unpredictable costs. Our comprehensive services include-
Security by
Design
ZEST Cybersecurity supports trust in systems, design and data, so organizations can take more risk, make transformational change and enable innovation with confidence.
Sector-based
Solutions
ZEST teams accomplish the mission by developing solutions that can be used to assure security and resilience of key business transformation initiatives and/or business functions.
Advisory, Managed Service and Implementation
And can be delivered to customers as part of a design, implementation or run phase of an engagement.
Infrastructure
support service
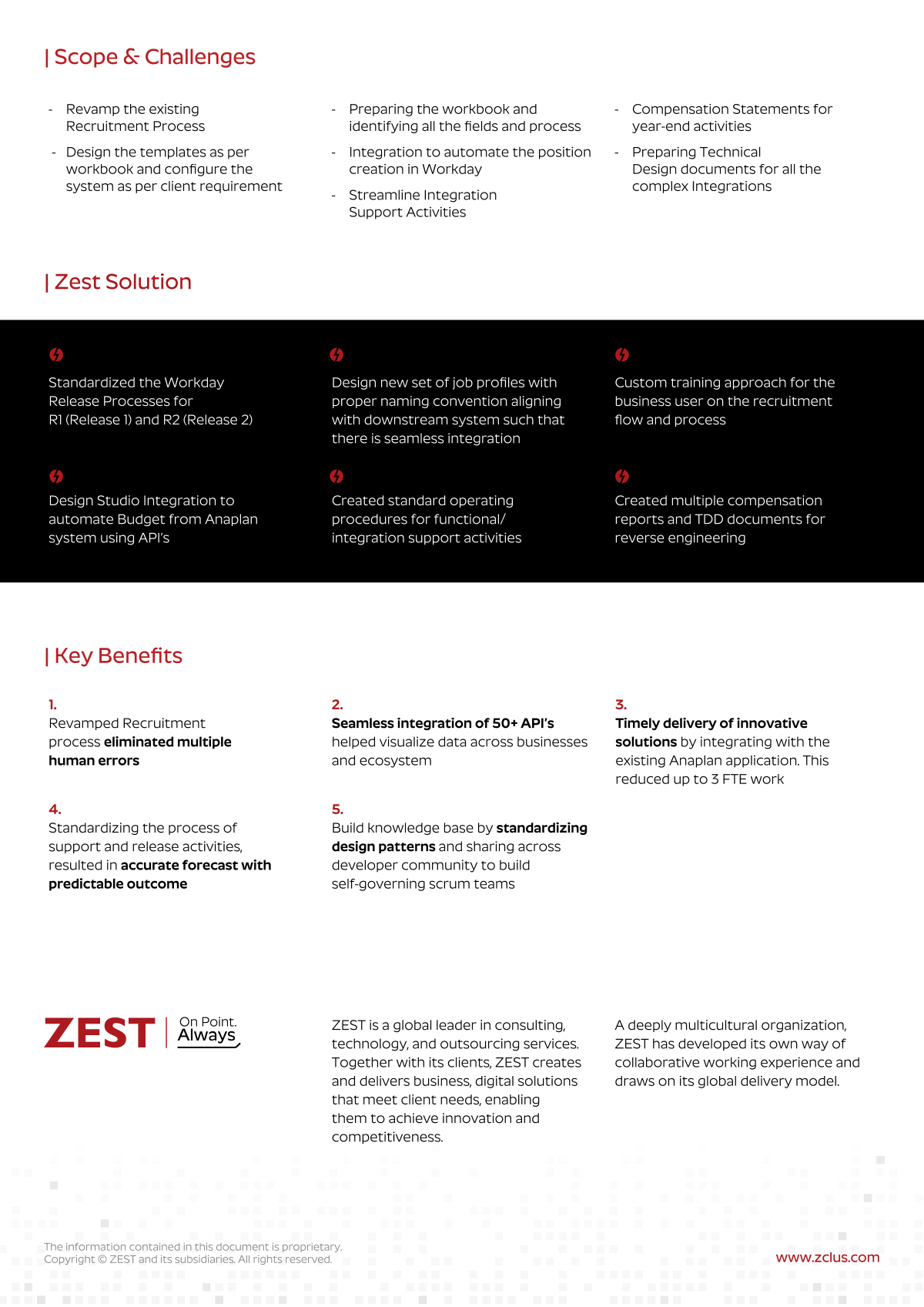
Our Service
Offerings
We provide top IT infrastructure support services. Our team will lead your outsourced IT infrastructure with care, modernizing platforms and technologies for enhanced agility and scalability with top infrastructure managed services.
IT Infrastructure Help Desk Management
We provide 24/7 support for your business user community to address all technical requests and IT inquiries, infrastructure management, enabling onsite & remote help desk architecture creation & management.
IT Application Infrastructure Support
We perform thorough remote app performance analytics, 24/7 functional & technical IT support, ensure policy compliance, and provide secure technology landscape
Cloud Support Services
We manage, secure, and optimize your existing cloud infrastructure to enable enhanced business alignment, operational efficiency, and process refinement.
Server Support Services
Our expert server IT support specialists perform server installations, configurations, upgrades, and other infrastructure management services to improve performance & reliability.
Network Support Services
We perform network design & architectural planning, audits, and ongoing support for TCP/IP setup, VPSs, SANs, LAN/WAN & media integrations, and network device troubleshooting.
Secure & Modernize Your IT Operations
By adopting, integrating, and implementing innovative technologies that keep your business systems up-to-date.
IT Infrastructure Security & Modernization
We perform vulnerability scans, SSL/AES encryptions, and other server security best practices for SQL Server, MySQL, PostgreSQL, Mongo DB, Oracle, Informix, Db2, and other databases.